The Privacy Rule of Health Insurance Portability and Accountability Act of 1996 (HIPAA) dictates the use and disclosure of Protected Health Information (PHI) by covered entities. Our ontological framework succinctly captures the complexity of HIPAA’s security and privacy protection.
Ontology of HIPAA Privacy Protection
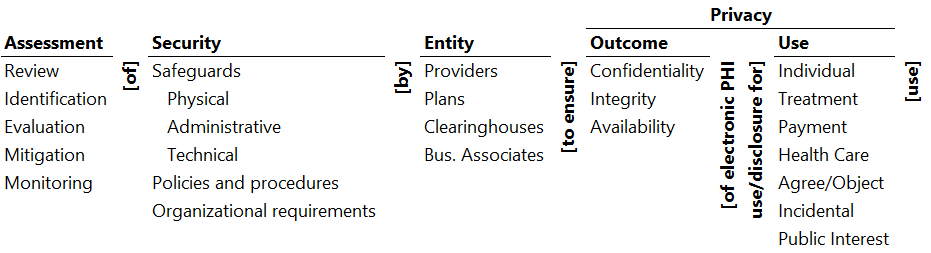
Illustrative Pathways
- Review of safeguards by providers to ensure confidentiality of electronic PHI use/disclosure for individual use.
- Evaluation of policies and procedures by plans to ensure integrity of electronic PHI use/disclosure for payment use.
- Monitoring of organizational requirements by clearinghouses to ensure availability of electronic PHI use/disclosure for public interest.
Glossary
- Assessment: Of the information system (IS) to assure security and privacy of personal health information (PHI).
- Review: Of data about the security of IS and privacy of PHI.
- Identification: Of the key issues (strengths and weaknesses) of IS for privacy of PHI.
- Evaluation: Of the impact of the strengths and weaknesses of IS on privacy of PHI.
- Mitigation: Of the negative impacts of IS security on PHI privacy.
- Monitoring: Of the IS compliance with PHI privacy requirements.
- Security: Control of access to PHI.
- Safeguards: Measures to control access to PHI.
- Physical safeguards: Physical limits on access to PHI.
- Administrative safeguards: Administrative limits on access to PHI.
- Technical safeguards: Information technology-based limits on access to PHI.
- Policies and procedures: Expectations that describe acceptable and unacceptable behavior.
- Organizational requirements: Requirements of itself and its business associates to assure security and privacy.
- Safeguards: Measures to control access to PHI.
- Entity: Organization responsible for assuring privacy of PHI.
- Providers: Of healthcare — clinics, hospitals, and allied organizations.
- Plans: Administrators of healthcare plans, insurance, etc.
- Clearinghouses: Processors or facilitators of processing of healthcare data.
- Business associate: A person who performs functions or activities on behalf of, or certain services for a covered entity.
- Privacy: Control of PHI and its use.
- Outcome: Control of PHI use.
- Confidentiality: Assuring the authorized disclosure of PHI and preventing unauthorized disclosure.
- Integrity: Assuring the trustworthiness of PHI and preventing unauthorized modification.
- Availability: Assuring the availability for authorized use and prevention of availability for unauthorized use.
- Use: Application of PHI for a purpose.
- Individual: For use by the patient/health consumer.
- Treatment: For treatment of the patient.
- Payment: For payment for services.
- Healthcare: For maintenance and improvement of physical and mental health.
- Agree/Object: For patient to agree or object to the use of his/her PHI.
- Incidental: Secondary uses or disclosures that cannot reasonably be prevented.
- Public interest: Use required by law, public health, health oversight activity, abuse, negligence, and research.
- Outcome: Control of PHI use.
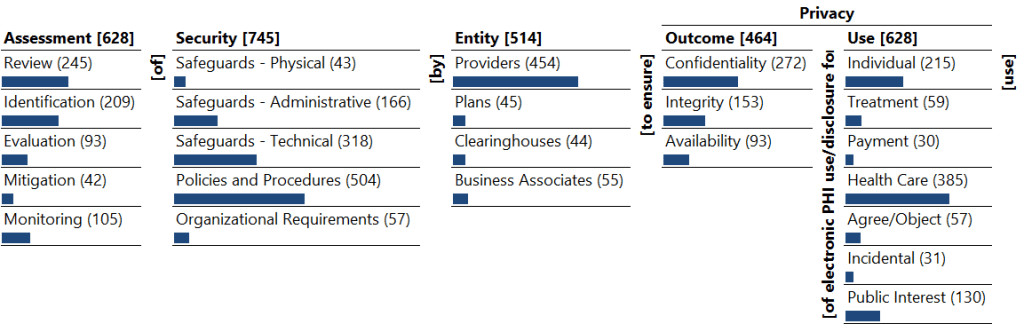
Monad Map
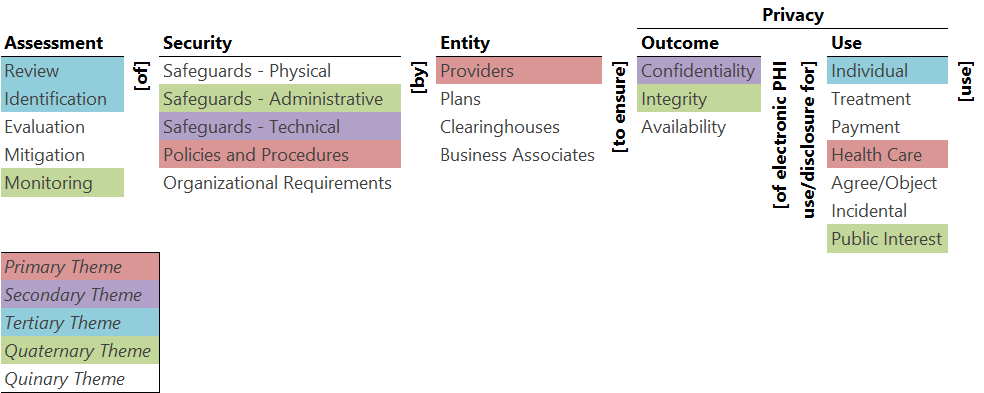
Theme Map
Related Links
Ontological Meta-Analysis and Synthesis of HIPAA
The Bright, Light, and Blind/Blank Spots in HIPAA Research: An Ontological Analysis

Leave a comment